
What Is Bitcoin
What Is BitCoin?
Maybe you’ve heard of
BitCoin—it
wants to shake the entire global economy. And some people think it
might! It’s online money—an alternative to dollars and euros. Well
what’s that mean? It’s complicated, but we break it down.
BitCoin is a digital currency…
BitCoin
is not real money. It’s an online “currency”—virtual tokens that can be
exchanged for goods and services at places that accept it, the same way
you’d give someone a dollar for a cookie.
with mega aspirations…
In their
YouTube manifesto,
BitCoin’s
creators say they’re going to revolutionize global finance the way the
web changed publishing. So! Kind of a lofty goal, aiming to be a global
currency up there with (or replacing) the dollar. Right now, that’s
still the pipiest of pipe dreams.
that’s exchanged via P2P
When you write your friend a check, money from your account is
withdrawn from your bank, and then transferred to her bank, and then she
withdraws it as cash (maybe). With
BitCoin,
there are no middlemen (other than the users that comprise the network
itself). Money goes straight from you to whomever, through the BitCoin
P2P system, with no intermediary agency passing along the chips.
and generated by its users.
This is where it starts to get a little weird! Unlike traditional
currency, that’s backed up by something, (be it gold, silver, or a
central bank), BitCoins are generated out of thin air. Through a process
called “mining,” a little app sits on your computer and slowly—very
slowly—creates new BitCoins in exchange for providing the computational
power to process transactions. When a new batch of coins is ready,
they’re distributed in probabilistic accordance to whomever had the
highest computing power in the mining process. The system is rigged so
that no more than 21 million BitCoins will ever exist—so the mining
process will yield less and less as time goes on, and more people sign
up. This makes the whole system a lot sweeter for early adopters.
To be spent at the few places BitCoin is accepted.
Not many places accept BitCoin at the moment, unlike traditional
currency. But! There’s decent incentive for small businesses to use
it—it’s free to use, and there aren’t any transaction fees. At the
moment you can buy the services of a web designer, indie PC games,
homemade jewelry, guns, and, increasingly, illegal drugs. If the
internet is the Wild West, BitCoin is its wampum.
or converted into real money.
Just like you can trade in yen for dollars, you can swap your
BitCoins with other users for several “real world” currencies. And right
now, the BitCoin is trading very high! As I write this, one BitCoin is
worth $7.5. Not too shabby at all.
Ways to earn bitcoins
Earn bitcoins online
Well to me bitcoins are the perfect online currency, makes it harder
for governments to trace transactions, however not entirely impossible,
but if you use your head you should be safe.
But you really dont have to invest to get into the bitcoin marked,
just start doing some work for bitcoins, there is a couple of good sites
for this online.
bitcoinclassifieds
forbitcoins.com
Also you could begin building an online business based on bitcoins,
perhaps the ebay for bitcoins, there is a lot of different sites with
bitcoins, if you like to gamble you could win some bitcoins from
bitcoinerr
a site for small jobs similiar to amazons mechanical turk ?
betco.in
the online pokerroom with only bitcoins, they got a lot of freerolls,
which is great but they really dont get a lot of their freerolls
running.
There also is a bitcoin web bank at
flexcoin.com
but that is a closed land for newcomers no invites, and I did not get
in, if anybody got in please send me an invite. I really want to join, I
am not sure but there was something about them going public, or was
that just for a start periode and then going private to only have
trusted members signed up, and then somebody gotta vouch for each new
member.
bitcoin pyramide
join the pyramide for me, and attract yourself a lot of referrals to get some bitcoins.
You can also
There is a lot of things you can do, that is you can make a service that takes payment in bitcoins.
This could be a good idea, as you can make payments more anonymous in
this way, as there is only a number, of course it is possible to dig
out who that account belongs to, but you can use instawallets for some
payments between the buyer and yourself and the thing is really hard to
track.
Ways to earn bitcoins
Earn bitcoins online
Well to me bitcoins are the perfect online currency, makes it harder
for governments to trace transactions, however not entirely impossible,
but if you use your head you should be safe.
But you really dont have to invest to get into the bitcoin marked,
just start doing some work for bitcoins, there is a couple of good sites
for this online.
bitcoinclassifieds
forbitcoins.com
Also you could begin building an online business based on bitcoins,
perhaps the ebay for bitcoins, there is a lot of different sites with
bitcoins, if you like to gamble you could win some bitcoins from
bitcoinerr
a site for small jobs similiar to amazons mechanical turk ?
betco.in
the online pokerroom with only bitcoins, they got a lot of freerolls,
which is great but they really dont get a lot of their freerolls
running.
There also is a bitcoin web bank at
flexcoin.com
but that is a closed land for newcomers no invites, and I did not get
in, if anybody got in please send me an invite. I really want to join, I
am not sure but there was something about them going public, or was
that just for a start periode and then going private to only have
trusted members signed up, and then somebody gotta vouch for each new
member.
bitcoin pyramide
join the pyramide for me, and attract yourself a lot of referrals to get some bitcoins.
You can also
There is a lot of things you can do, that is you can make a service that takes payment in bitcoins.
This could be a good idea, as you can make payments more anonymous in
this way, as there is only a number, of course it is possible to dig
out who that account belongs to, but you can use instawallets for some
payments between the buyer and yourself and the thing is really hard to
track.
what is bitcoin,
what is bitcoin mining,
what is bitcoin
used for, what is bitcoin worth, what is bitcoin backed by, what is
bitcoin farming, what is bitcoin address, what is bitcoind, what is
bitcoin difficulty, what is bitcoin
youtube, what is bitcoin mining,
what is bitcoin mining actually doing,
what is bitcoin worth, what is bitcoin currency, what is bitcoin
farming, what is bitcoin address, what is bitcoin used for, what is
bitcoin plus, how to earn bitcoins, how to earn bitcoins online, how to
earn bitcoins mining, how to earn bitcoins mining, how to earn free
bitcoins, how long to earn bitcoin, how to earn more bitcoins,
how to earn money with bitcoin,
easy ways to earn bitcoins, generate bitcoins, how do i get bitcoins,
how to make bitcoins, online bitcoin mining, where do bitcoins come
from, make money mining bitcoins, easy bitcoin mining
 The gsmmap.org Live ISO is a boot image (not to be confused with GSM MAP dissector Wireshark) to capture GSM data from an Osmocom BB-supported mobile and upload them for analysis at gsmmap.org. ISO is based on Debian Linux 2.6.32.5 kernel. The main goal of this project is to create GSM map describing the geographical distribution of GSM networks along with analyze of impersonation, interception and tracking possibilities -> disclosing security problems of GSM networks. A script automatically starts at login That guides through the process. Starting system is pretty easy and can be accomplished in few minutes using VirtualBox. If you are lost, please follow awesome gsmmap.org Live ISO Tutorial first.
The gsmmap.org Live ISO is a boot image (not to be confused with GSM MAP dissector Wireshark) to capture GSM data from an Osmocom BB-supported mobile and upload them for analysis at gsmmap.org. ISO is based on Debian Linux 2.6.32.5 kernel. The main goal of this project is to create GSM map describing the geographical distribution of GSM networks along with analyze of impersonation, interception and tracking possibilities -> disclosing security problems of GSM networks. A script automatically starts at login That guides through the process. Starting system is pretty easy and can be accomplished in few minutes using VirtualBox. If you are lost, please follow awesome gsmmap.org Live ISO Tutorial first. 





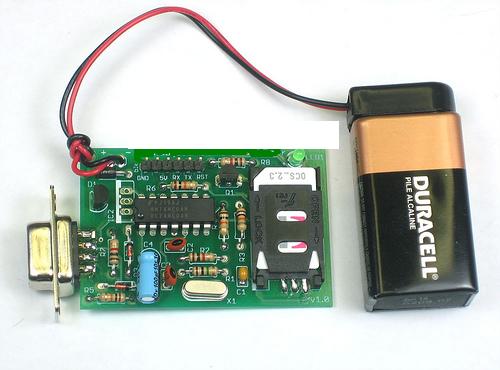
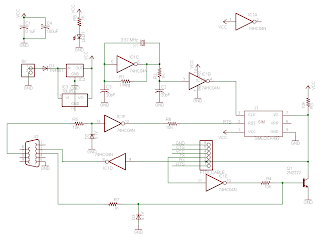
















 Theme interception of mobile phones is currently very topical, in Slovakia it is doubly true.
Theme interception of mobile phones is currently very topical, in Slovakia it is doubly true.





 Some time ago I wrote a short
Some time ago I wrote a short 










